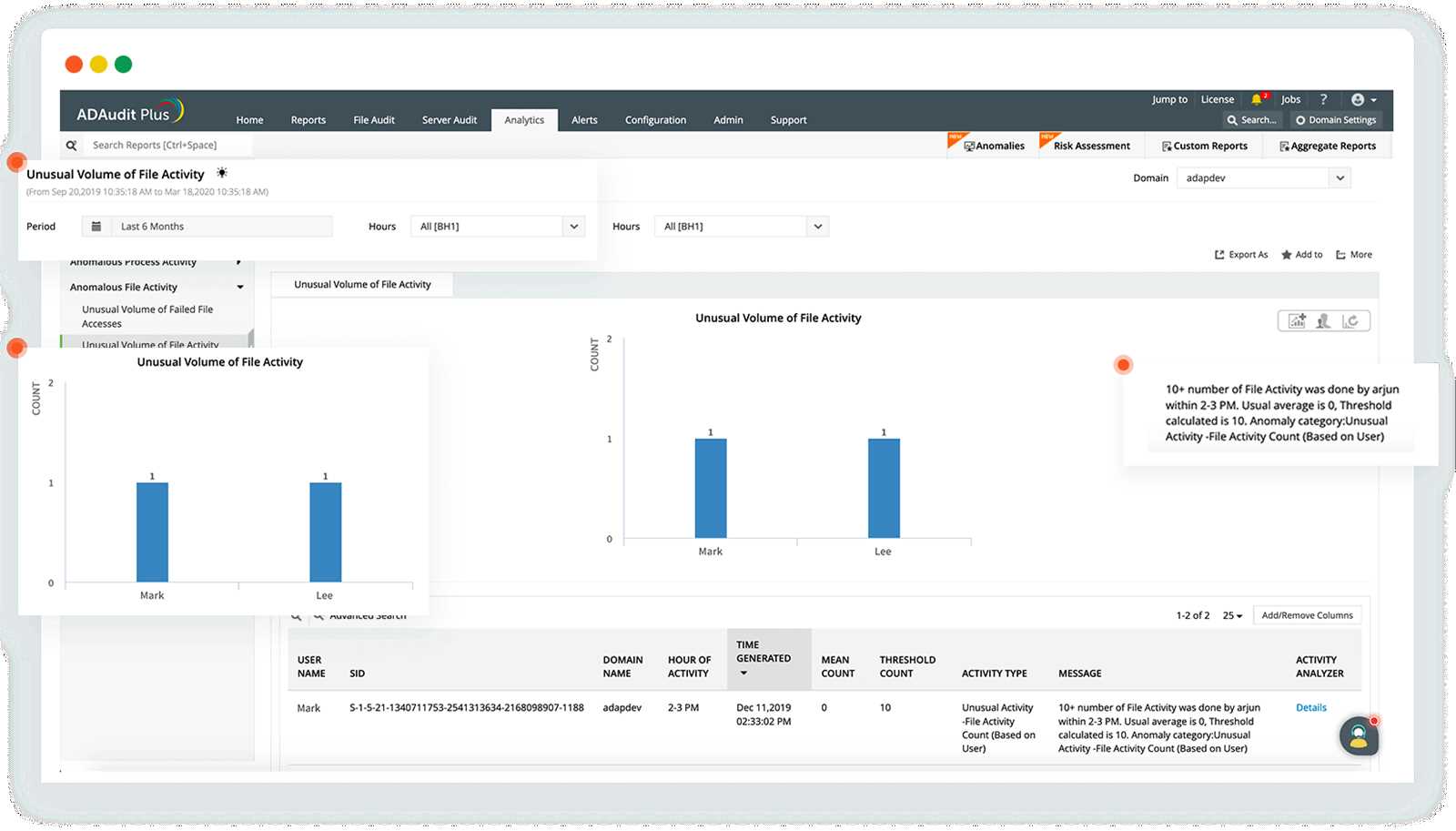
In today’s environment, protecting sensitive information from internal dangers is more critical than ever. Employees and contractors, who have direct access to organizational systems, can unintentionally or intentionally compromise security. This section delves into the types of risks associated with internal actors and emphasizes the need for strong security practices in every organization.
Recognizing potential dangers within the workplace requires a thorough understanding of how they manifest. By focusing on the behavior patterns of individuals with authorized access, organizations can identify vulnerabilities and take proactive measures. Prevention is always better than dealing with the consequences of a breach, which is why this knowledge is crucial for all personnel.
To safeguard company assets and maintain a safe working environment, everyone must stay informed about common risks. Regular assessments, training, and policy reviews are essential to ensure that everyone can identify and address these concerns effectively. The responsibility for maintaining security lies with all members of the organization, and awareness is the first step toward achieving this goal.
Insider Threat Awareness Exam Insights
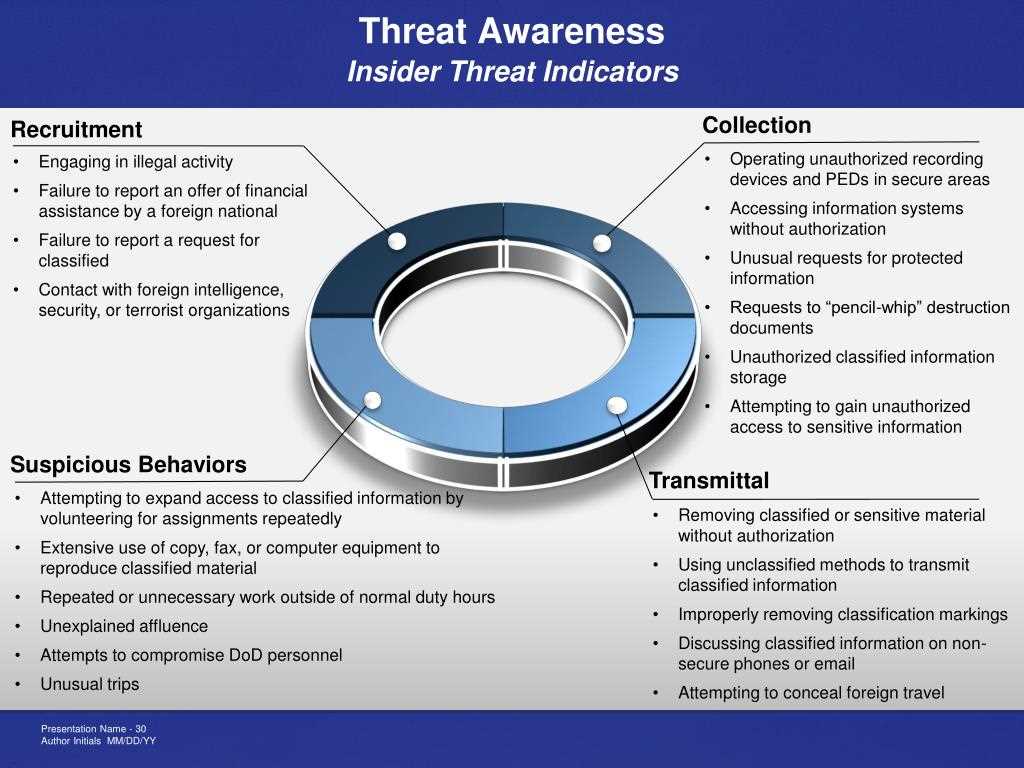
Understanding the complexities of internal security risks is crucial for anyone responsible for safeguarding sensitive company data. The goal is not only to recognize potential dangers but also to learn how to mitigate them effectively. This section provides key insights into tackling internal risks and strengthening your defense strategies.
Recognizing the Key Factors
Effective defense starts with knowing the common factors that lead to internal vulnerabilities. Key considerations include:
- Employee access to sensitive information
- Lack of proper security protocols
- Inadequate monitoring and oversight
- Training gaps among staff members
Practical Strategies for Improvement
Once the risks are understood, the next step is implementing actionable strategies to address them. Some effective measures include:
- Conducting regular security training for all employees
- Enforcing strict access control policies
- Establishing clear reporting channels for suspicious activities
- Reviewing and updating security protocols frequently
By staying vigilant and proactive, organizations can prevent significant issues before they escalate. Continuous improvement is essential to maintaining a secure environment, and everyone plays a role in the process.
Understanding the Importance of Insider Threats
Securing an organization from internal risks is a fundamental aspect of any comprehensive security strategy. While much attention is often placed on external vulnerabilities, internal actors with authorized access to sensitive data can pose significant risks. Recognizing the gravity of these risks is essential for maintaining robust protection measures across the workplace.
The importance of addressing internal risks lies in their potential to cause serious damage. Individuals with the right access can inadvertently or intentionally compromise data, leading to financial loss, reputational damage, or legal consequences. It is crucial for every organization to understand the potential impact these risks can have on operations.
Key Factors That Make Internal Risks Dangerous
- Privileged access to critical systems
- Lack of transparency in internal operations
- Weaknesses in employee monitoring and reporting
- Challenges in identifying malicious intent among trusted personnel
Steps to Mitigate the Risks
To prevent internal risks from escalating, organizations must adopt comprehensive security practices, including:
- Implementing strict access control protocols
- Regularly conducting security training for all employees
- Establishing clear guidelines for reporting suspicious activities
- Continuously monitoring user activity and system access logs
By taking these steps, businesses can create a safer environment that reduces the likelihood of internal compromises and strengthens overall security posture.
Key Concepts in Threat Identification
Identifying potential risks within an organization is essential for preventing any form of data compromise or security breach. By recognizing specific patterns and behaviors, businesses can stay one step ahead of those who may exploit internal access. This section highlights fundamental ideas related to spotting and understanding these risks effectively.
Recognizing Risk Indicators

One of the first steps in detecting internal risks is understanding the common indicators that suggest something may be wrong. These may include:
- Unusual access patterns or unauthorized attempts
- Inconsistent employee behavior or sudden changes in actions
- Discrepancies between system activity and normal workflows
- Excessive access to sensitive data without clear justification
Common Motives Behind Risks
Understanding the potential motives behind individuals’ actions is another key concept. These motives can vary, but common reasons for security breaches include:
- Financial gain
- Revenge or personal vendettas
- Negligence or lack of knowledge
- External pressure or manipulation
By understanding these key concepts, organizations can develop a sharper focus on identifying, addressing, and preventing risks that may arise from within.
Common Scenarios and Case Studies
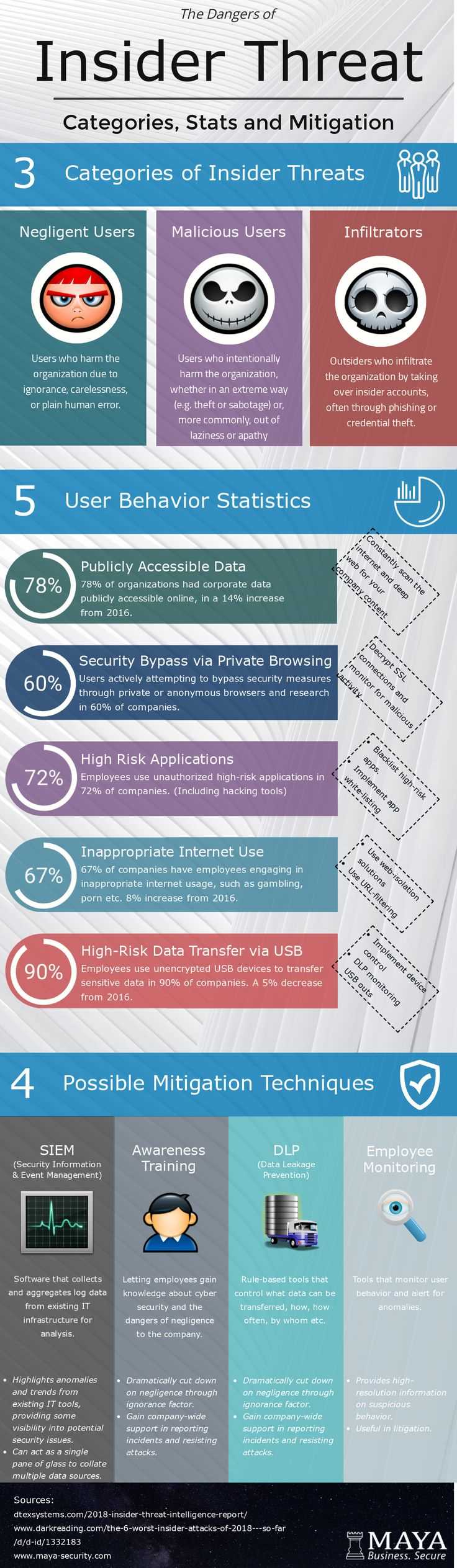
Understanding real-life examples of security breaches caused by internal actors provides valuable insights into potential vulnerabilities. Analyzing these situations helps organizations learn how to detect similar risks and avoid similar outcomes. This section presents several case studies that highlight common risks and how they can manifest within an organization.
Case Study 1: Data Theft by a Trusted Employee
In this case, a well-placed employee with access to sensitive client data began copying large volumes of information without clear authorization. The employee’s behavior was initially unnoticed, but after an investigation, it was revealed that the individual was planning to sell the data to competitors. This case demonstrates the importance of monitoring access to critical systems and implementing audit trails.
Case Study 2: Unintentional Breach Due to Negligence
Another scenario involves an employee accidentally sending sensitive files to the wrong email address. While the breach was not intentional, it exposed valuable company data to an external entity. This case emphasizes the need for clear procedures regarding handling sensitive information and the importance of employee training to minimize human error.
By studying these and similar cases, organizations can develop a deeper understanding of how internal risks can lead to significant security incidents. Implementing proper protocols and continually educating staff are crucial steps in preventing these types of events.
Strategies for Preventing Insider Attacks
Effective prevention of internal security risks requires a comprehensive approach that focuses on policies, employee behavior, and monitoring systems. By implementing robust strategies, organizations can minimize the potential for damage caused by individuals with authorized access to sensitive information. This section highlights the best practices for safeguarding critical assets from within.
Key Preventative Measures
The following table outlines key strategies for reducing the likelihood of internal breaches:
| Strategy | Description |
|---|---|
| Access Control | Implement strict policies to limit access to sensitive data based on roles and responsibilities. |
| Regular Audits | Conduct frequent audits of employee activities and system usage to detect any unusual patterns. |
| Employee Training | Provide ongoing training to staff on security practices and the importance of safeguarding sensitive information. |
| Clear Reporting Channels | Establish transparent procedures for employees to report suspicious activities or concerns anonymously. |
| Behavioral Monitoring | Utilize monitoring tools to track employees’ access to and handling of critical systems and data. |
Creating a Secure Work Environment
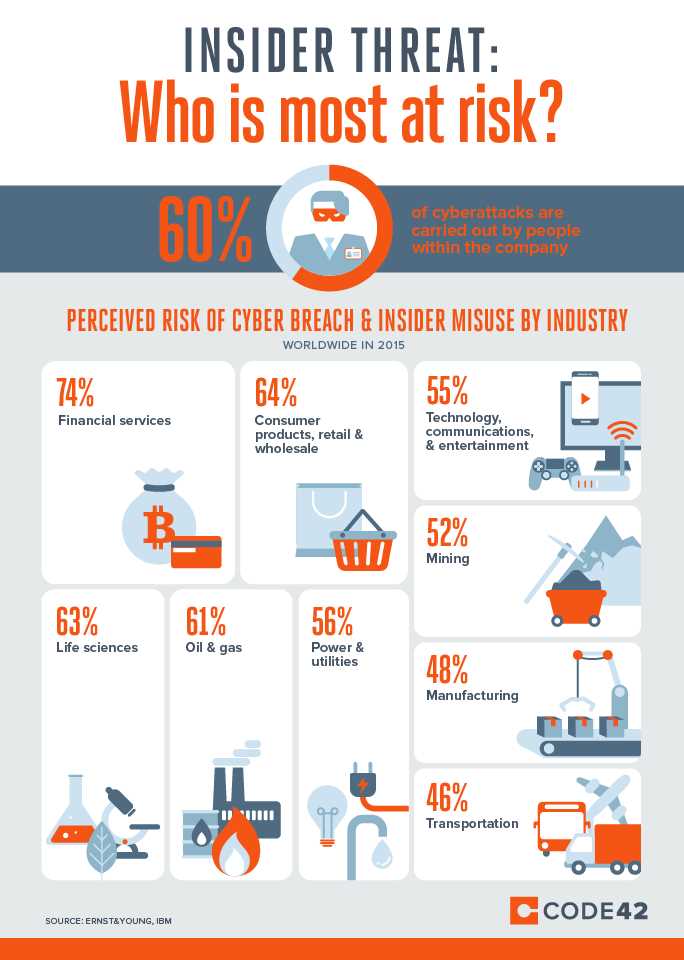
Beyond implementing technical measures, fostering a security-conscious culture is vital. Regular communication, clear policies, and leadership support play significant roles in creating an environment where security is prioritized. By encouraging employees to report unusual activities and remain vigilant, organizations can significantly reduce their vulnerability to internal risks.
Exam Preparation Tips and Best Practices
Preparing for an evaluation on security risks caused by internal actors requires strategic planning and a structured approach. A solid understanding of key concepts, along with practice and review, will increase confidence and readiness. This section offers practical tips and best practices for effective preparation.
Start by reviewing essential topics and understanding the underlying principles. Breaking down the material into manageable sections and setting up a study schedule can help prevent last-minute cramming. Make use of available resources, such as study guides, practice tests, and group discussions, to reinforce learning and identify areas that need further attention.
Additionally, focus on understanding how to apply theoretical knowledge to real-world situations. Case studies and scenarios are often included in assessments to test practical application. By reviewing these examples and practicing problem-solving, you can better prepare for the challenges presented during the evaluation.
How to Apply Your Knowledge in Real Life
Understanding security risks and how to prevent them is important, but knowing how to apply this knowledge effectively in real-world situations is equally crucial. In this section, we will explore how to translate theoretical concepts into practical actions that protect sensitive information and systems within an organization.
Adopting Preventative Measures
One of the first steps to applying your knowledge is integrating preventative measures into daily operations. This can include establishing access control protocols, monitoring employee behavior, and ensuring that systems are secure from potential vulnerabilities. By consistently implementing these practices, you can reduce the likelihood of harmful actions from individuals within your organization.
Creating a Culture of Vigilance

Another important aspect is fostering a culture of awareness among your colleagues. Educating your peers on security best practices, encouraging them to report any suspicious behavior, and reinforcing the importance of safeguarding sensitive information can make a significant difference. When everyone understands their role in maintaining security, the organization as a whole becomes more resilient to potential risks.