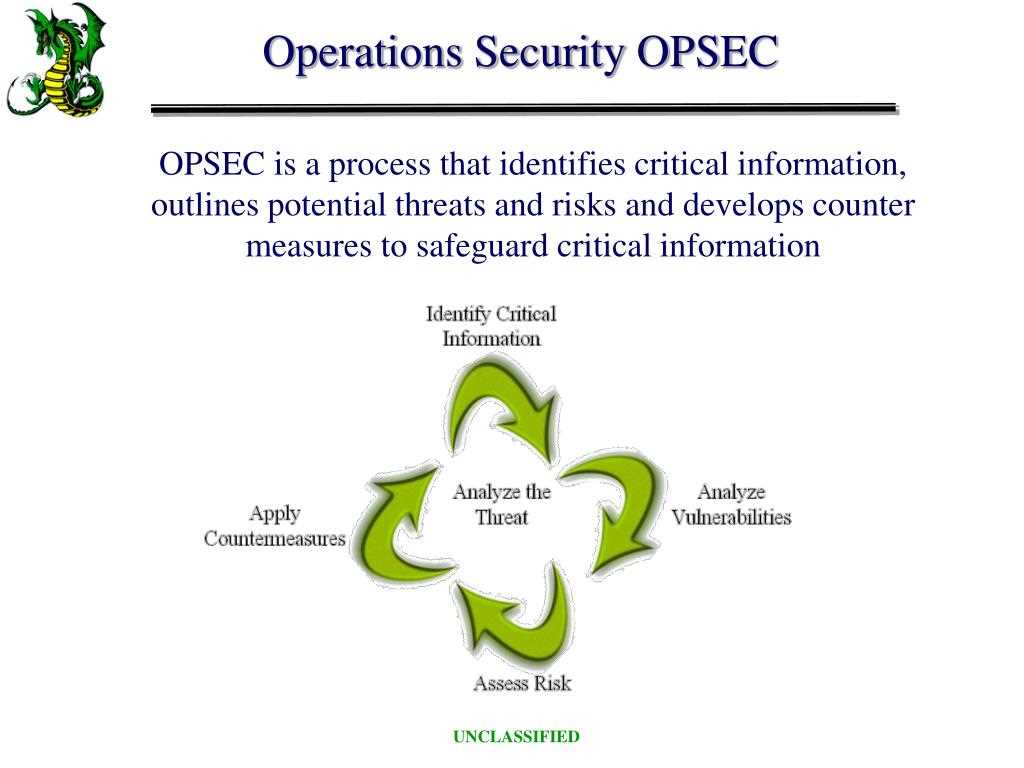
Ensuring the safety and confidentiality of sensitive information is a critical aspect of any organization. The ability to assess and evaluate security measures effectively helps in identifying potential risks and vulnerabilities. By mastering the process of security assessments, individuals and teams can ensure a robust defense against external threats and internal weaknesses. This section explores the fundamental principles behind these evaluations and provides insights into how to approach such tasks with precision and expertise.
Essential Knowledge for Successful Security Evaluation
Understanding key security principles is the foundation of any successful evaluation. It involves grasping concepts such as risk management, threat identification, and the importance of safeguarding data from unauthorized access. A solid grasp of these core elements allows individuals to perform their roles effectively and contribute to the overall safety of the organization.
Key Areas to Focus On
- Risk Assessment: Identifying and evaluating potential threats.
- Confidentiality and Integrity: Ensuring data is secure and accurate.
- Security Protocols: Adhering to best practices for defense mechanisms.
Preparing for Evaluation Challenges
As you engage in the process of evaluating security measures, being prepared for potential challenges is crucial. Familiarize yourself with common pitfalls and how to avoid them. Regular updates to your knowledge and practice will keep you ahead of any new threats or vulnerabilities that might arise.
Effective Methods to Excel in Security Evaluations

Successful completion of these assessments often requires applying the right strategies. Focus on continuous learning and testing your knowledge through various scenarios. By engaging in regular evaluations and practicing with different security contexts, you can enhance your skills and remain prepared for real-world applications.
Tips for Improvement
- Study relevant case studies and past evaluations to learn from others’ experiences.
- Regularly review and update your knowledge to stay current with security trends.
- Practice applying theoretical knowledge in practical, hands-on situations.
Application of Skills in Real-World Scenarios
Once the foundational knowledge is in place, applying those skills in real-world scenarios is essential. Practicing within actual organizational settings helps refine strategies and ensures a comprehensive understanding of security measures. Through ongoing practice, individuals can become proficient in identifying vulnerabilities and mitigating risks effectively.
Understanding Security Protocols and Their Importance
In the realm of digital protection, safeguarding sensitive data and ensuring privacy are of utmost importance. The process of evaluating and improving security strategies is crucial for maintaining the integrity of systems and protecting against various types of threats. This section delves into the essential aspects of security assessments, offering a comprehensive view of the necessary skills and practices needed to excel in protecting critical assets.
Key Concepts in Cybersecurity and Security Measures
The foundation of effective cybersecurity lies in understanding core principles such as threat identification, risk management, and data protection. Gaining a deep understanding of these areas allows individuals to properly identify vulnerabilities and devise strong countermeasures. Implementing these concepts efficiently can significantly reduce the likelihood of security breaches.
Preparing for Security Evaluations
Preparation is a key aspect of any evaluation process. Being well-versed in common risks and mitigation strategies helps participants in making informed decisions during assessments. Keeping up to date with the latest developments in the field is crucial for ensuring thorough evaluations and the ability to anticipate emerging threats.
Study Methods for Achieving Success in Security Evaluations
Successful evaluations depend largely on how well one prepares. Focused study techniques, such as reviewing case studies, practicing with real-world scenarios, and regularly testing knowledge, are highly effective methods. By engaging with different materials and simulation tools, individuals can ensure they are well-prepared for any evaluation or security challenge.
Common Pitfalls in Security Practices
It’s important to be aware of frequent mistakes made during security evaluations. Common errors include failing to prioritize risks, not considering all possible threats, or misinterpreting key security protocols. These mistakes can lead to inadequate protection and may expose systems to greater vulnerabilities. Avoiding such errors requires continuous learning and attention to detail.
How to Answer Security Evaluation Questions Accurately
Answering security questions with precision requires a clear understanding of the principles and practices involved. Focusing on clarity, logical reasoning, and evidence-based responses helps in formulating correct solutions. Strong analytical skills and the ability to apply knowledge to varied situations are essential for success.
Mastering Security Practices and Protocols
Mastery of security principles is achieved through consistent application and ongoing education. By staying informed about the latest tools, techniques, and vulnerabilities, professionals can stay ahead in the constantly evolving field of digital protection. Practicing security measures regularly helps refine skills and build confidence in real-world situations.
Practical Uses of Security Evaluation Insights
The insights gained from security evaluations are valuable for practical application. By understanding the outcomes and challenges of previous assessments, individuals can improve their strategies and implement more effective measures. These insights also offer the opportunity to refine risk management techniques and ensure the ongoing safety of data and systems.