
A penetration testing proposal PDF is a comprehensive document that outlines the scope, objectives, and methodology of a planned penetration testing project. This proposal is specifically designed for clients who are interested in improving their cybersecurity posture by identifying vulnerabilities and weaknesses in their systems and networks.
The penetration testing proposal PDF provides a detailed overview of the testing process, including the tools and techniques that will be used to simulate real-world attacks on the client’s infrastructure. It also highlights the benefits of conducting a penetration test, such as identifying potential entry points for hackers, evaluating the effectiveness of security controls, and providing recommendations for improving overall security.
In addition to explaining the testing process, the proposal also includes information on the qualifications and experience of the penetration testing team, as well as a breakdown of the pricing and timeline for the project. This ensures transparency and allows the client to make an informed decision about whether to proceed with the proposed testing.
Overall, a penetration testing proposal PDF is an essential document in the cybersecurity industry, providing clients with a clear understanding of the testing process and the potential benefits it can bring to their organization. By presenting the information in a concise and professional format, the proposal sets the stage for a successful partnership between the client and the penetration testing team.
Understanding the Importance of Penetration Testing Proposal PDF
Penetration testing is a critical process for any organization looking to ensure the security of their digital assets. A penetration testing proposal PDF is an essential tool in effectively communicating the scope and objectives of a penetration testing project to stakeholders. This document serves as a roadmap for the testing process and outlines the steps that will be taken to identify and exploit vulnerabilities in the organization’s network and systems.
One of the primary benefits of using a penetration testing proposal PDF is that it provides a clear and concise overview of the testing process. It details the specific techniques and methodologies that will be used, as well as the timeline for testing and reporting. By presenting this information in a well-organized and visually appealing format, the proposal PDF helps the stakeholders understand the depth of the testing process and the potential impact it can have on the organization’s security.
Furthermore, a penetration testing proposal PDF enables the organization to clearly define the scope of the testing project. This includes identifying the systems and applications that will be tested, as well as any specific vulnerabilities or threats that need to be addressed. By clearly defining the project scope, the proposal PDF helps the organization prioritize its security efforts and allocate resources effectively.
In addition, a penetration testing proposal PDF can also serve as a valuable marketing tool. It can be shared with potential clients or partners to demonstrate the organization’s commitment to security and its proactive approach to identifying and mitigating vulnerabilities. The proposal PDF can showcase the organization’s expertise in penetration testing and provide evidence of successful past projects.
In conclusion, a penetration testing proposal PDF is a crucial document for organizations looking to ensure the security of their digital assets. It helps communicate the scope and objectives of the testing project, defines the project scope, and can serve as a marketing tool. By investing time and effort into creating a comprehensive and visually appealing proposal PDF, organizations can effectively convey the importance of penetration testing and the value it brings to their overall security strategy.
Benefits of Penetration Testing Proposal PDF
Penetration testing is a crucial component of any comprehensive cybersecurity strategy. It involves simulating an attack on a computer system, network, or application to identify potential vulnerabilities and weaknesses. A well-prepared penetration testing proposal in PDF format offers numerous benefits for both the organization conducting the test and the client.
1. Clear and Comprehensive Documentation: A penetration testing proposal in PDF format provides a clear and structured document that outlines the scope, objectives, and methodologies of the test. It ensures that all parties involved have a shared understanding of the testing process and its goals.
2. Professional Presentation: Presenting a penetration testing proposal in PDF format demonstrates professionalism and attention to detail. The proposal can be easily shared and printed, ensuring that all stakeholders have access to the same information and can review it at their convenience.
3. Enhanced Security: The use of a PDF format for the penetration testing proposal minimizes the risk of tampering or unauthorized access. PDF files can be protected with passwords or digital signatures, ensuring that the proposal remains secure throughout the evaluation process.
4. Efficient Communication: The PDF format allows for efficient communication between the testing team and the client. The proposal can be easily emailed or shared via cloud storage platforms, ensuring that all parties have instant access to the document and can provide feedback or ask questions in a timely manner.
5. Easy Reference and Documentation: A well-structured PDF document allows for easy reference and documentation. It provides a standardized format that can be used for storing, organizing, and retrieving important information related to the penetration testing process, including the results, recommendations, and corrective actions.
6. Legally Binding Document: A penetration testing proposal in PDF format can be considered a legally binding document between the testing team and the client. It ensures that all parties are aware of their rights and responsibilities, reducing the risk of misunderstandings or disputes during or after the testing process.
In conclusion, utilizing a well-prepared penetration testing proposal in PDF format offers numerous benefits. It provides clear documentation, enhances security, facilitates efficient communication, allows for easy reference and documentation, and can be considered a legally binding document. These advantages ultimately contribute to the success and effectiveness of the penetration testing process.
Key Components of a Penetration Testing Proposal PDF
A penetration testing proposal PDF is a crucial document that outlines the scope, approach, and deliverables of a penetration testing project. To ensure that a proposal is comprehensive and effectively communicates the goals and objectives of the engagement, there are several key components that should be included.
1. Executive Summary
The executive summary provides a high-level overview of the penetration testing proposal, summarizing the key objectives, timelines, and deliverables. It should clearly outline the purpose of the engagement and highlight the potential risks and vulnerabilities that will be addressed through the testing process.
2. Scope of Work
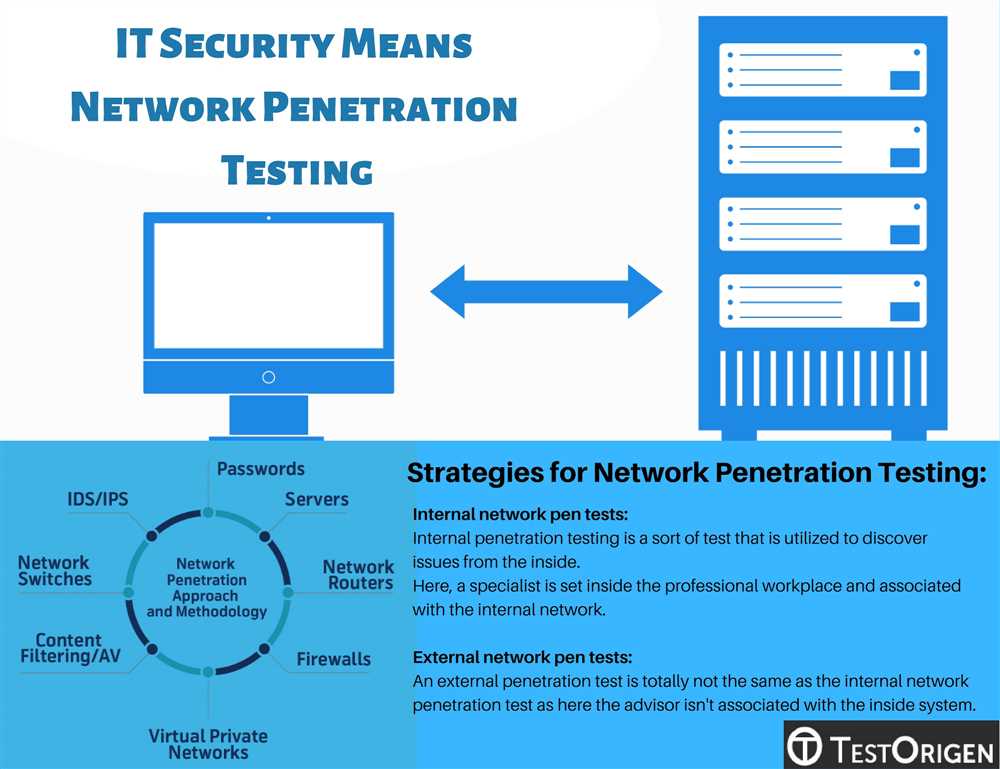
The scope of work section defines the boundaries and limitations of the penetration testing engagement. This includes specifying the systems, networks, and applications that will be tested, as well as any specific testing methodologies or tools that will be utilized. It should also outline any exclusions or areas that will not be covered during the engagement.
3. Methodology
The methodology section details the approach and techniques that will be employed during the penetration testing process. This may include a combination of automated and manual testing methods, as well as a description of the reconnaissance, vulnerability scanning, and exploitation phases. It should also address any legal and ethical considerations that will be followed.
4. Deliverables
The deliverables section outlines the specific outputs and reports that will be provided at the conclusion of the penetration testing engagement. This may include a detailed report of vulnerabilities discovered, recommended remediation steps, and a summary of findings and recommendations. It should also specify the format and timeline for delivering these documents.
5. Team Qualifications
The team qualifications section highlights the expertise and experience of the penetration testing team that will be conducting the engagement. This may include certifications, relevant industry experience, and examples of previous successful engagements. It should provide confidence in the team’s abilities to effectively identify and address vulnerabilities.
6. Project Timeline and Cost
The project timeline and cost section outlines the estimated duration of the engagement and the associated costs. This includes the number of testing days required, any additional expenses, and the overall project budget. It should also address any specific milestones or checkpoints throughout the engagement.
Overall, a well-structured and comprehensive penetration testing proposal PDF is essential for effectively communicating the objectives, scope, and deliverables of a penetration testing engagement. By including these key components, organizations can ensure that the proposal accurately reflects their needs and expectations, and helps to establish a clear understanding between the organization and the penetration testing team.
Scope and Objectives
In this penetration testing proposal, the scope and objectives of the testing are outlined. The main purpose of the engagement is to assess the security of the target system and identify any potential vulnerabilities that could be exploited by adversaries. The scope of the testing will include both external and internal assessments, covering all aspects of the system, including network infrastructure, operating systems, applications, and data storage.
The objectives of the penetration testing are to:
- Identify and assess any weaknesses or vulnerabilities in the target system that could lead to unauthorized access or compromise of sensitive data.
- Evaluate the effectiveness of existing security controls and mechanisms in place.
- Test for potential Privilege Escalation, Denial of Service, and other common attack vectors.
- Provide recommendations for strengthening the overall security posture of the target system.
This engagement will simulate real-world attack scenarios, utilizing a combination of automated tools and manual techniques to identify and exploit vulnerabilities. The testing will be conducted by a team of experienced penetration testers, who will follow a structured methodology and adhere to ethical guidelines throughout the engagement.
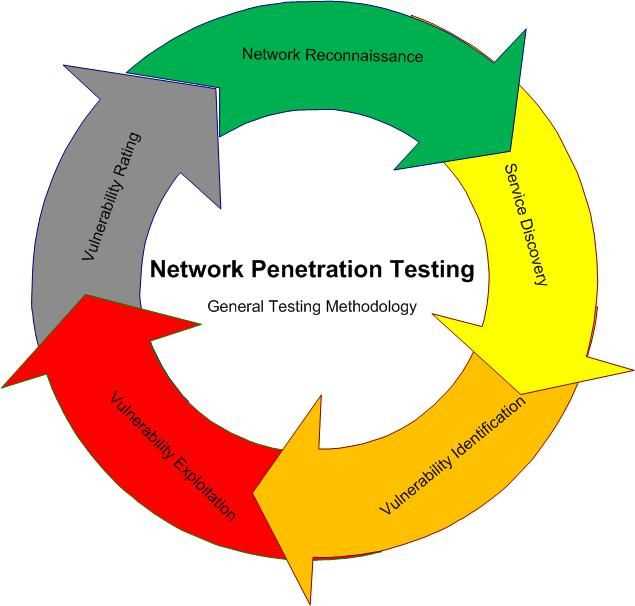
Methodology
A comprehensive and structured methodology is essential for conducting an effective penetration test. Our team follows a proven approach that encompasses several key steps, ensuring a thorough evaluation of your system’s security.
1. Reconnaissance
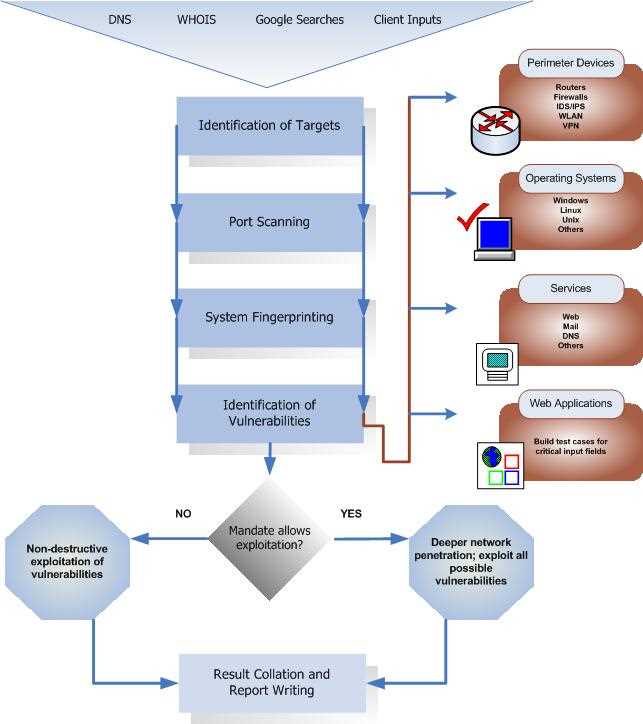
The first step in our methodology is reconnaissance, where we gather information about your organization’s infrastructure, systems, and network. This includes conducting open-source intelligence (OSINT) research, reviewing publicly available information, and performing network scanning.
2. Vulnerability Assessment
After gathering the necessary information, we proceed with performing a vulnerability assessment. This involves using specialized tools and techniques to identify potential vulnerabilities in your infrastructure, such as misconfigurations, outdated software, or weak security settings.
3. Exploitation
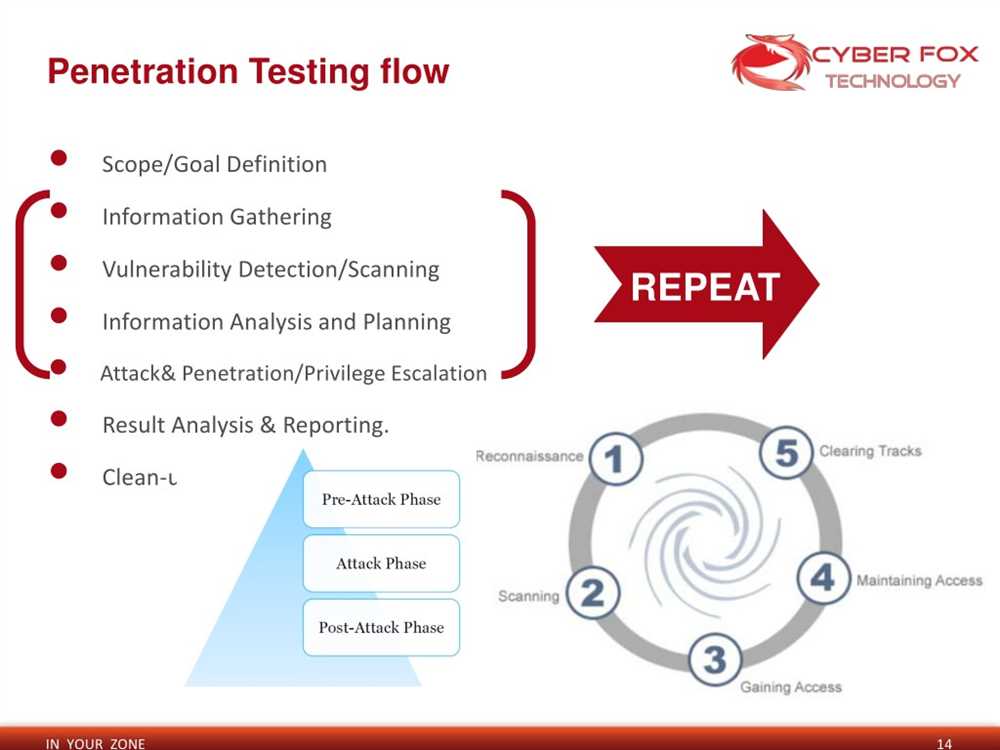
Once vulnerabilities have been identified, our team moves on to the exploitation phase. This step involves attempting to exploit the identified vulnerabilities to gain unauthorized access to your systems or execute malicious code. We employ a range of tactics, including social engineering, password cracking, and network-specific exploits.
4. Post-Exploitation
After successfully exploiting vulnerabilities, we evaluate the impact of the compromise and assess the potential damage that a real attacker could cause. This step allows us to better understand the risks associated with the vulnerabilities and provide recommendations for mitigation.
5. Reporting
Finally, we provide a detailed report highlighting the vulnerabilities discovered, their severity, and the potential impact on your organization. Our report includes actionable recommendations for improving your system’s security, prioritized based on the level of risk they pose.
Deliverables
In this section, we outline the proposed deliverables for the penetration testing project. These deliverables are designed to provide a comprehensive assessment of the target system’s security vulnerabilities and provide actionable recommendations for improving its overall security posture.
1. Penetration Testing Report:
Upon completion of the penetration testing engagement, we will provide a detailed report that includes a comprehensive overview of the testing methodology, findings, and recommendations. This report will be organized in a clear and concise manner, making it easy for stakeholders to understand and prioritize the identified vulnerabilities.
The report will include:
- An executive summary highlighting the key findings and recommendations.
- A detailed description of the testing methodology used.
- A comprehensive list of all identified vulnerabilities, including their severity level and potential impact.
- Recommendations for addressing each identified vulnerability, including prioritization based on risk level.
2. Technical Vulnerability Assessment:
In addition to the penetration testing report, we will provide a technical vulnerability assessment that includes a thorough examination of the target system’s network and application vulnerabilities. This assessment will identify areas of weakness that can be exploited by attackers and provide recommendations for remediation.
The technical vulnerability assessment will include:
- A comprehensive scan of the target system’s network infrastructure, including open ports, services, and potential security vulnerabilities.
- An analysis of the target system’s web applications, looking for common vulnerabilities such as SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF).
- Identification of any configuration issues or insecure practices that may expose the target system to unnecessary risk.
- Recommendations for addressing each identified vulnerability, including best practices for securing network infrastructure and web applications.
Overall, these deliverables will provide a holistic view of the target system’s security vulnerabilities and offer actionable recommendations for improving its overall security posture.