In the rapidly evolving world of cybersecurity, organizations and individuals are constantly seeking ways to protect their systems from malicious attacks. Ethical hacking, or penetration testing, has emerged as a crucial tool in this battle. The Pentester Blueprint PDF is a comprehensive guide that equips aspiring pentesters with the knowledge and skills to identify vulnerabilities in computer systems and networks.
Written by industry experts, this blueprint covers essential topics such as reconnaissance, vulnerability assessment, exploitation, and post-exploitation. It provides an in-depth understanding of both common and advanced hacking techniques, enabling readers to gain a holistic view of the pentesting process.
The Pentester Blueprint PDF goes beyond theoretical concepts, offering practical, hands-on exercises and real-world scenarios to reinforce learning. Readers will learn how to conduct ethical hacking assessments using tools and technologies commonly employed by professionals in the field. By following the step-by-step instructions provided, they can develop the necessary skills to systematically evaluate a system’s security posture and recommend effective remediation strategies.
Whether you are an IT professional looking to transition into a career in cybersecurity or an ethical hacker seeking to enhance your skillset, The Pentester Blueprint PDF is an indispensable resource. With its comprehensive coverage and practical approach, it serves as a valuable reference guide, empowering readers to understand the methodologies and techniques used by hackers, thereby enabling them to better defend against real-world cyber threats.
The Pentester Blueprint PDF
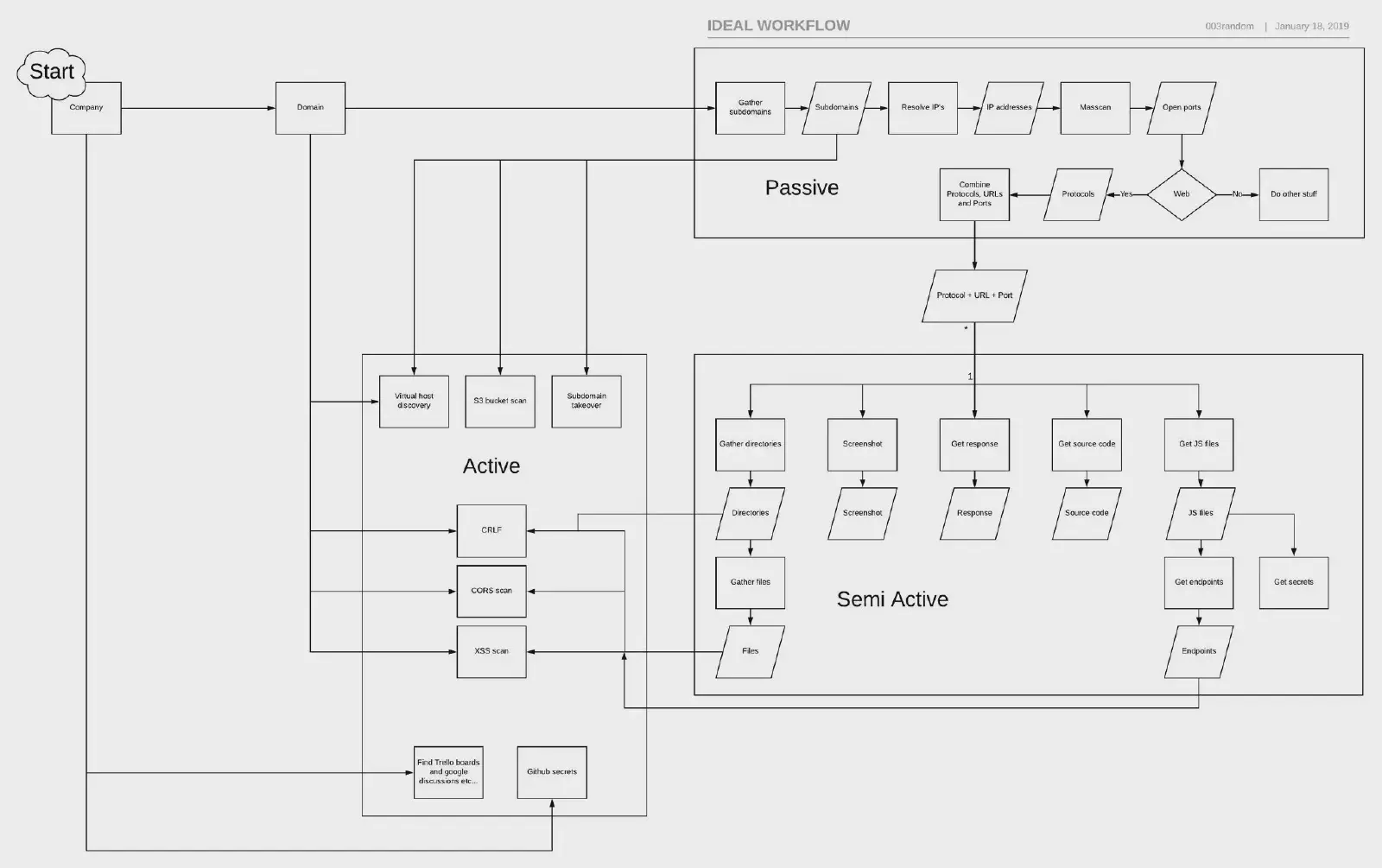
The Pentester Blueprint PDF is a comprehensive guide that provides aspiring or experienced pentesters with the necessary knowledge and skills to excel in their field. This blueprint covers a wide range of topics, including penetration testing methodologies, tools, and techniques.
One of the key advantages of the Pentester Blueprint PDF is its ability to condense a vast amount of information into a concise and organized format. The guide is structured in a way that allows readers to easily navigate through different topics and quickly find the information they need.
The guide starts by introducing the fundamentals of penetration testing, providing readers with a solid understanding of the concepts and principles that underpin this field. It then progresses to more advanced topics such as network scanning, vulnerability assessment, and exploitation techniques.
The Pentester Blueprint PDF also includes numerous real-world examples and case studies, allowing readers to apply their knowledge in practical scenarios. This hands-on approach not only helps reinforce learning but also provides valuable insights into the challenges faced by pentesters in real-world situations.
In addition to the technical aspects of penetration testing, the guide also covers other important aspects such as legal and ethical considerations. This is crucial for pentesters to ensure they adhere to applicable laws and regulations and maintain a high level of professionalism in their work.
Overall, the Pentester Blueprint PDF serves as an invaluable resource for anyone looking to pursue a career in penetration testing or enhance their existing skills. Its comprehensive coverage and practical approach make it an essential tool for aspiring pentesters.
What is The Pentester Blueprint?
The Pentester Blueprint is a comprehensive guide designed to provide aspiring ethical hackers with the necessary knowledge and skills to excel in the field of penetration testing. This blueprint offers a structured learning path, covering various topics such as network security, web application security, wireless security, and social engineering. It aims to equip individuals with the practical skills needed to identify and exploit vulnerabilities in computer systems and networks.
By following The Pentester Blueprint, individuals can gain a deep understanding of the tools, techniques, and methodologies used by professional penetration testers. The blueprint offers step-by-step instructions, real-world examples, and hands-on exercises to enhance the learning experience. Whether you are a beginner or an experienced professional looking to expand your skills, The Pentester Blueprint can serve as an invaluable resource.
Key Features of The Pentester Blueprint:
- Structured learning path covering various areas of penetration testing
- In-depth coverage of network security, web application security, wireless security, and social engineering
- Step-by-step instructions and practical exercises for hands-on learning
- Real-world examples and case studies to illustrate concepts
- Focus on industry-standard tools and methodologies used by professional penetration testers
- Updated and relevant content to keep up with the evolving cybersecurity landscape
Whether you are interested in starting a career in ethical hacking or looking to enhance your existing skills, The Pentester Blueprint is an essential resource that can help you develop the knowledge and expertise required to succeed in the field of penetration testing.
Benefits of The Pentester Blueprint
1. Practical Approach: The Pentester Blueprint offers a practical and hands-on approach to learning and mastering the art of penetration testing. Unlike traditional theoretical courses, this blueprint focuses on real-world scenarios and provides step-by-step guidance on how to effectively identify and exploit vulnerabilities. By following the blueprint, aspiring pentesters can gain practical experience and develop the skills necessary to succeed in the field.
2. Comprehensive Learning: The Pentester Blueprint covers a wide range of topics and techniques relevant to penetration testing. From reconnaissance and scanning to exploitation and post-exploitation, this blueprint provides a comprehensive learning experience that spans the entire penetration testing process. By following the blueprint, pentesters can gain a deep understanding of the different phases involved in a successful penetration test and acquire the knowledge needed to effectively execute each phase.
- Hands-on Labs: One of the key advantages of The Pentester Blueprint is its emphasis on hands-on labs. The blueprint provides practical exercises and lab scenarios that allow learners to apply the knowledge they have acquired in a real-world setting. By completing these labs, aspiring pentesters can gain practical experience and develop their skills in a controlled environment.
- Industry-Recognized Certification: The Pentester Blueprint prepares learners for industry-recognized certifications such as the Offensive Security Certified Professional (OSCP) exam. By successfully completing this certification, individuals can demonstrate their proficiency in penetration testing and increase their employment opportunities.
- Community Support: The Pentester Blueprint has a strong and supportive community that offers guidance, assistance, and collaboration opportunities. Learners can connect with fellow pentesters, share knowledge, and participate in discussions to enhance their learning experience. The community support fosters a collaborative learning environment and provides access to valuable resources and insights.
- Career Advancement: The skills acquired through The Pentester Blueprint can open doors to exciting career opportunities in the field of cybersecurity. With the growing demand for skilled pentesters, individuals who have mastered the blueprint can pursue careers as penetration testers, security consultants, or ethical hackers. The practical knowledge gained through the blueprint can also serve as a solid foundation for further professional development and specialization.
In conclusion, The Pentester Blueprint offers numerous benefits for individuals looking to pursue a career in penetration testing. From its practical approach and comprehensive learning materials to its hands-on labs, industry-recognized certification, community support, and career advancement opportunities, this blueprint provides a holistic and effective learning experience for aspiring pentesters.
How to Use The Pentester Blueprint
The Pentester Blueprint is a comprehensive guide that outlines the necessary steps and tools to become a successful pentester. Whether you are a beginner or an experienced professional, this blueprint provides valuable insights and resources for anyone interested in the field of penetration testing.
To make the most out of The Pentester Blueprint, it is important to follow a systematic approach. First, familiarize yourself with the different phases of penetration testing, including reconnaissance, scanning, gaining access, and maintaining access. Each phase requires a specific set of skills and tools, and the blueprint provides detailed guidance on these areas.
Throughout the blueprint, you will find recommended tools and techniques for each phase of penetration testing. These tools range from open-source software to commercial solutions, and it is crucial to experiment and find the ones that work best for your specific needs. Additionally, the blueprint emphasizes the importance of staying updated with the latest vulnerabilities and exploits, as the field of pentesting is constantly evolving.
Furthermore, the blueprint encourages hands-on practice and continuous learning. It is not enough to simply read about penetration testing – you must actively engage with the material and gain practical experience. Setting up a lab environment and conducting your own penetration tests is a valuable way to apply the knowledge gained from the blueprint and develop your skills.
In conclusion, The Pentester Blueprint is an indispensable resource for anyone interested in becoming a pentester. By following the step-by-step guidance, utilizing the recommended tools and techniques, and consistently practicing and learning, you can develop the necessary skills and knowledge to excel in the field of penetration testing.
Key Components of The Pentester Blueprint
When it comes to the pentester blueprint, there are several key components that are essential for success. These components include:
1. Tools and Software
One of the most important aspects of the pentester blueprint is having the right tools and software. This includes tools for network scanning, vulnerability assessment, and exploit development. Some popular tools include Nmap, Metasploit, and Wireshark. Having a comprehensive set of tools will enable the pentester to identify vulnerabilities and exploit them effectively.
2. Knowledge and Expertise
Another crucial component of the pentester blueprint is knowledge and expertise. Pentesters need to have a deep understanding of different operating systems, network protocols, programming languages, and security vulnerabilities. They should also be well-versed in various hacking techniques and methodologies. Continuous learning and staying up-to-date with the latest security trends is essential in this field.
3. Methodology and Frameworks
A solid methodology and frameworks are essential for conducting effective penetration testing. This includes having a structured approach to identify and exploit vulnerabilities. Popular frameworks such as the Open Web Application Security Project (OWASP) Testing Guide and Penetration Testing Execution Standard (PTES) provide guidelines and methodologies for performing penetration tests. Adhering to a standardized methodology ensures consistency and accuracy in the testing process.
4. Communication and Reporting
Effective communication and reporting skills are crucial for pentesters. They need to be able to clearly convey findings and vulnerabilities to both technical and non-technical stakeholders. A well-written and detailed report is essential for clients to understand the risks and take appropriate remediation steps. Additionally, pentesters should be able to communicate with other team members and collaborate effectively during testing engagements.
5. Ethical and Professional Conduct
Lastly, maintaining ethical and professional conduct is a key component of the pentester blueprint. Pentesters must adhere to ethical standards and legal boundaries while performing their duties. They should respect client confidentiality and follow industry best practices. Professional conduct includes being honest, accountable, and responsible for the work performed. Building trust with clients is essential for long-term success in this field.
In conclusion, the pentester blueprint requires a combination of tools, knowledge, methodology, communication skills, and ethical conduct. Keeping these key components in mind will help pentesters in achieving successful and impactful penetration testing engagements.
Advantages of Using The Pentester Blueprint PDF
The Pentester Blueprint PDF offers several advantages for individuals interested in becoming skilled penetration testers. This comprehensive guide provides a structured approach to learning and mastering the necessary skills and techniques required for successful penetration testing.
One of the main advantages of using The Pentester Blueprint PDF is its easy accessibility. Being in PDF format, it can be easily downloaded and accessed from various devices, such as laptops, smartphones, and tablets. This allows individuals to study and practice penetration testing techniques at their convenience, whether they are at home, in the office, or on the go.
The Pentester Blueprint PDF also offers a well-organized and systematic learning path. It provides a step-by-step guide that covers essential topics, including network reconnaissance, vulnerability assessment, exploitation, and post-exploitation. This organized approach helps individuals grasp the concepts and build upon their knowledge progressively.
Additionally, the PDF format allows for easy navigation and quick referencing. The content is divided into sections, making it easy to locate specific topics or revisit previous ones for review. This makes The Pentester Blueprint PDF a valuable resource for both beginners and experienced professionals in the field of penetration testing.
Furthermore, The Pentester Blueprint PDF includes practical exercises and hands-on labs, which allow individuals to apply their knowledge in a real-world setting. These exercises help hone skills and reinforce understanding of the concepts covered in the guide. By actively practicing and experimenting with the techniques outlined in the PDF, individuals can develop the practical skills necessary for a successful career in penetration testing.
In conclusion, The Pentester Blueprint PDF offers numerous advantages for individuals interested in becoming skilled penetration testers. Its easy accessibility, organized learning path, and practical exercises make it an invaluable resource for anyone looking to master the art of penetration testing.