
In today’s world, securing sensitive materials and ensuring proper handling of confidential data are critical aspects of organizational operations, especially within government agencies. Every individual involved in handling this type of content is required to undergo specific assessments to confirm their knowledge and ability to protect these resources effectively.
These evaluations focus on several key principles, including privacy protection, classification protocols, and appropriate safeguarding practices. Individuals must demonstrate an understanding of best practices and compliance with the security measures outlined by their respective institutions.
Proper preparation for these evaluations is essential. By familiarizing oneself with the underlying guidelines and regulations, participants can ensure they are ready to manage confidential materials securely and contribute to maintaining a high level of protection within their workplace.
Introduction to Sensitive Data Management
Protecting specific categories of sensitive materials is essential for maintaining national security and organizational integrity. These materials are not classified at the highest levels but still require careful handling and secure protocols. The handling of such resources involves understanding how to safeguard and share them responsibly within legal and regulatory frameworks.
The proper management of these assets ensures that unauthorized individuals do not gain access to content that could potentially jeopardize operational security. It involves adherence to specific policies designed to mitigate risks while facilitating necessary access for authorized personnel.
Effective protection of sensitive content relies on a clear understanding of guidelines that govern its usage, storage, and transmission. This knowledge is essential for anyone working with these materials to avoid breaches or mishandling that could lead to severe consequences.
Importance of Compliance with Military Standards
Adhering to established guidelines is crucial for maintaining the security and integrity of critical assets. Military organizations set rigorous standards to ensure that sensitive materials are protected from unauthorized access, mishandling, or potential threats. Compliance with these standards is not optional; it is vital for national security and effective operations.
Following these regulations guarantees that all personnel are well-informed about the procedures for securing and distributing sensitive data. Failure to comply with these guidelines can lead to severe consequences, including compromising security, exposing vulnerabilities, or even legal ramifications.
- Ensures protection against unauthorized access.
- Reduces the risk of data leaks and security breaches.
- Facilitates safe sharing and distribution of materials between authorized entities.
- Maintains operational readiness and trust within the organization.
In essence, compliance strengthens the overall security infrastructure, ensuring that sensitive resources are handled with the highest level of responsibility and care.
Ensuring Proper Handling and Protection

Assessments designed to evaluate knowledge of security protocols play a crucial role in ensuring that personnel understand how to handle sensitive materials appropriately. By confirming that individuals are equipped with the necessary skills, these evaluations contribute directly to the protection of valuable data and assets. The process helps organizations maintain high standards for confidentiality, privacy, and compliance with regulatory requirements.
Through a series of well-structured questions, participants are tested on their understanding of the best practices for securing and managing sensitive content. These assessments aim to verify that individuals are capable of recognizing potential risks and responding effectively to secure all classified or restricted assets within their roles.
| Security Aspect | Role in Maintaining Security |
|---|---|
| Proper Handling | Ensures materials are protected from unauthorized access and misuse. |
| Risk Awareness | Prepares individuals to identify and mitigate potential security threats. |
| Compliance Knowledge | Ensures that personnel are familiar with the necessary policies and procedures. |
In this way, evaluations serve as a vital component in safeguarding national security, reducing the likelihood of security breaches, and ensuring that only authorized personnel can access and handle sensitive materials. This proactive approach to training and assessment helps maintain secure environments within organizations.
Key Topics Addressed in the Assessment
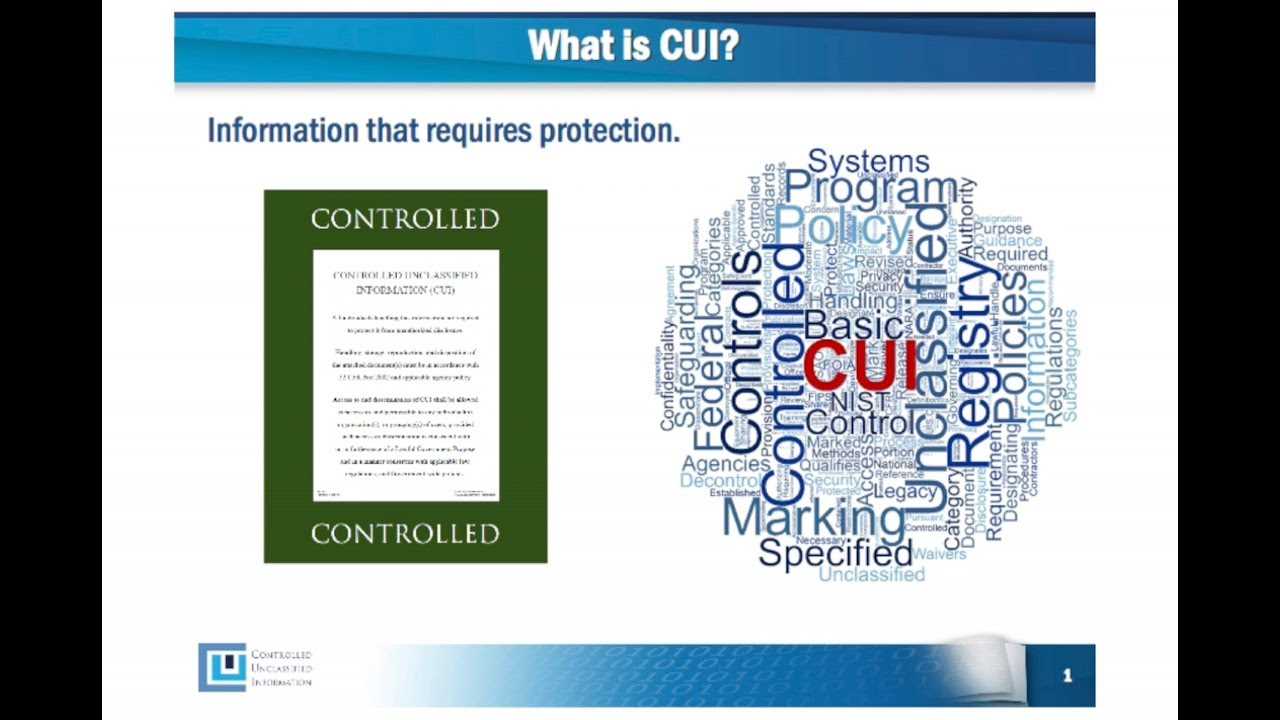
Evaluations designed to measure security awareness cover a range of critical areas, ensuring that individuals are well-versed in proper protocols for handling sensitive materials. These topics are essential to creating a secure environment and minimizing the risk of data breaches or mishandling of confidential resources. By addressing these key areas, the assessment ensures that personnel are fully prepared to manage these assets responsibly and effectively.
Understanding Security Protocols
One of the primary topics focuses on the fundamental security protocols that guide the handling and storage of sensitive data. Personnel must be familiar with procedures that prevent unauthorized access and safeguard the confidentiality of materials. This includes proper labeling, secure storage methods, and encryption techniques for protecting data during transit.
Compliance with Legal and Regulatory Guidelines
Another critical area covered is compliance with the various laws and regulations governing the use and distribution of sensitive content. Individuals are expected to demonstrate their knowledge of both national and organizational standards, ensuring they understand their responsibilities in maintaining secure systems. Awareness of the consequences of non-compliance is also an important aspect of this training.
Understanding Key Areas of Focus
When participating in security assessments, it’s essential to avoid common pitfalls that can lead to mistakes and misunderstandings. These errors can result in incorrect responses, jeopardizing the evaluation and potentially failing to meet compliance standards. Proper preparation and attention to detail are key to navigating the process successfully.
Misunderstanding Security Protocols
A frequent mistake is failing to fully understand the security procedures that must be followed. Clear comprehension of protocols for handling sensitive content, including storage, transmission, and disposal methods, is critical. Misinterpreting these guidelines can lead to serious security lapses and non-compliance.
Neglecting Legal and Regulatory Knowledge
Another common error is not being fully aware of the legal requirements surrounding the management of sensitive data. It is crucial to be familiar with both the regulations and the legal responsibilities regarding access and distribution. Ignorance of these requirements can result in incorrect answers and potential violations of critical rules.
Resources to Help You Prepare Effectively
Preparing for assessments related to security protocols requires access to reliable and comprehensive materials. A well-rounded approach includes studying guidelines, using available training resources, and gaining hands-on experience to understand the best practices for protecting sensitive content. Utilizing these resources will help ensure success during the evaluation process.
Official Guidelines and Handbooks
One of the most reliable sources of information is the official documentation provided by the relevant authorities. These handbooks and guidelines outline the security measures, procedures, and legal requirements that need to be followed. Reviewing these materials thoroughly will give you a solid foundation in security best practices and help you avoid common mistakes.
Online Training and Tutorials
Another excellent resource is online training programs and tutorials, which offer interactive learning experiences. These platforms often provide real-life scenarios and quizzes that simulate the real challenges faced when handling sensitive materials. Taking advantage of these resources can help reinforce your understanding and improve your preparedness for the assessment.