
Organizations face significant challenges when it comes to protecting sensitive information from internal sources. While much focus is placed on external cyber threats, risks originating from within can be just as damaging. Employees, contractors, and other trusted individuals often have access to critical systems, making it essential to recognize potential vulnerabilities in this area.
Recognizing the signs of risky behavior in the workplace is key to maintaining a secure environment. Effective training and proactive monitoring can help detect any unusual actions early, reducing the likelihood of data breaches or other disruptions. It is not just about preventing attacks but also about creating a culture where vigilance and security are part of everyday practices.
Knowing how to identify potential risks from those closest to your organization is vital. By equipping your team with the knowledge and tools to spot red flags, you can better safeguard your company’s assets. The process involves understanding common patterns of risky behavior and addressing them before they escalate into larger security issues.
What is an Internal Security Risk?
When a person within an organization exploits their position to cause harm, whether intentionally or unintentionally, it poses a serious concern for the business. These individuals often have access to critical data, systems, and internal processes, making them capable of inflicting significant damage if their actions go undetected. This form of vulnerability can range from data theft to sabotage, and it can be difficult to spot without proper precautions in place.
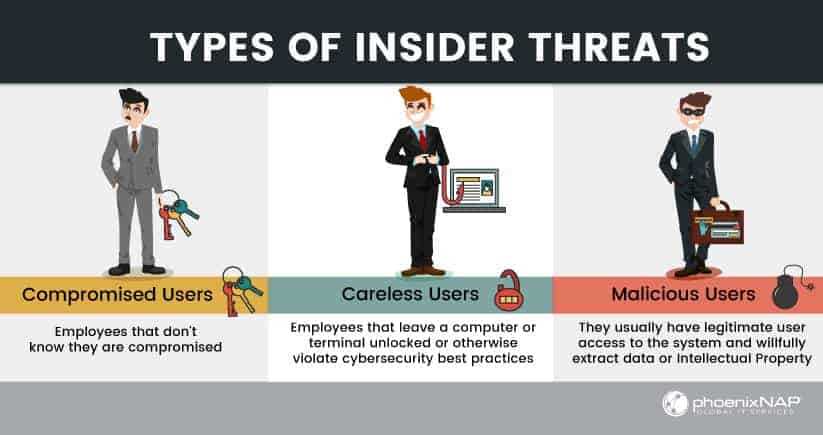
Types of Internal Security Risks
These risks can manifest in various ways, from employees misusing their access privileges to contractors gaining unauthorized control over sensitive information. Even well-meaning individuals might unknowingly expose company assets by failing to follow established security protocols or by being influenced by external factors. Regardless of the intent, the potential consequences remain substantial.
Why These Risks Are Hard to Detect
What makes these risks particularly challenging is the trust placed in individuals who hold internal access. Unlike external cyberattacks, which can be monitored through network defenses, internal vulnerabilities often go unnoticed until they have already caused damage. Regular monitoring, clear policies, and employee education are crucial to minimize such risks.
Why Internal Security Awareness Matters
Organizations must prioritize understanding the risks that come from within their workforce. Without proper recognition and management, individuals with internal access can compromise company data, systems, and resources. Creating an informed workforce is essential to ensure that potential risks are addressed before they escalate.
The following points highlight why it is crucial to focus on internal security:
- Preventing Data Loss – Unauthorized access to sensitive information can lead to significant data breaches that may harm the company’s reputation and bottom line.
- Minimizing Operational Disruption – Individuals with internal access can unintentionally or intentionally disrupt operations, leading to downtime or a loss of business continuity.
- Reducing Financial Risks – A security lapse can result in costly legal fees, regulatory penalties, or remediation expenses.
- Enhancing Employee Trust – When employees understand the importance of security practices, it fosters a culture of trust and collaboration within the organization.
By educating all levels of the workforce on the risks they may pose, organizations can better manage and reduce these risks. Proactive measures, such as regular training and clear guidelines, ensure that everyone remains vigilant and follows best practices in handling sensitive information.
Key Concepts in Risk Detection
To effectively safeguard an organization, it is crucial to understand the key principles behind identifying potential vulnerabilities. Risk detection is a proactive approach to recognizing actions or behaviors that could jeopardize an organization’s data and systems. By focusing on these concepts, businesses can better prevent damage caused by internal or external sources.
Behavioral Indicators
One of the most critical aspects of risk detection is identifying behavioral changes in individuals who may pose a potential risk. Unusual actions, such as accessing files outside their normal scope of work or attempting to bypass security protocols, can signal suspicious behavior. Recognizing these red flags early helps to mitigate risks before they escalate.
Data Monitoring and Anomaly Detection
Continuous monitoring of data and system activity is essential for identifying anomalies. Patterns that deviate from the norm, such as sudden spikes in data access or unusual login times, can provide valuable insights into potential security concerns. Tools that automate this process can help detect irregularities that might otherwise go unnoticed by human observation.
How to Identify Suspicious Behavior
Recognizing signs of unusual activity is crucial to maintaining the security of any organization. Individuals engaging in questionable actions may not always be easy to identify, but there are several common behaviors that often serve as indicators of potential risks. Understanding and monitoring these behaviors allows for timely intervention before any harm occurs.
Common Indicators of Unusual Actions
There are several key behavioral patterns to watch for when assessing whether someone is acting suspiciously. These can be subtle but noticeable over time if you know what to look for. Some of these signs may include:
| Behavior | Possible Risk |
|---|---|
| Accessing files or systems not related to their role | Potential data misuse or theft |
| Frequent after-hours activity or logins | Unauthorized actions during off-peak times |
| Attempting to bypass security protocols | Intentional harm or compromise of systems |
| Sudden, unexplained changes in behavior or attitude | Possible stress or external influence affecting judgment |
Tools for Detecting Unusual Activity
Automated tools and systems are increasingly used to detect deviations from normal patterns of behavior. These systems analyze login times, data access frequency, and other actions that can highlight irregularities. By combining human oversight with technology, organizations can spot potential risks earlier and take appropriate action to prevent further damage.
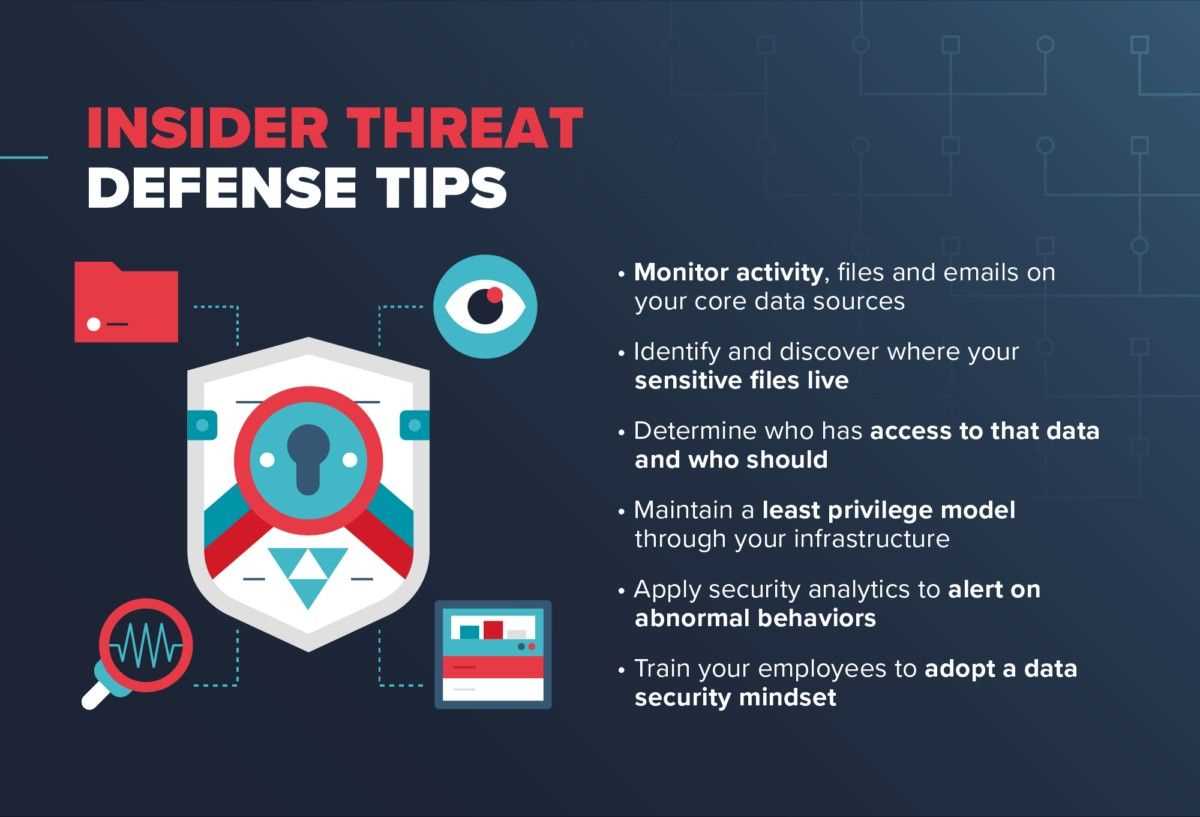
Effective Prevention Strategies for Organizations
Protecting sensitive information and ensuring the integrity of internal systems require proactive measures. A combination of preventive techniques, clear policies, and continuous monitoring can significantly reduce the risk of harm caused by those with internal access. By implementing a range of strategies, organizations can safeguard their assets and maintain a secure working environment.
Employee Education and Training is one of the most effective ways to mitigate risks. Regular training on security best practices and potential dangers equips employees with the knowledge to act responsibly. It also fosters a culture of vigilance, where everyone plays a role in maintaining security.
Access Control Systems should be tailored to restrict access based on the principle of least privilege. By ensuring that employees only have access to the information necessary for their roles, organizations limit the scope of damage in case of a breach. Regular audits of access rights ensure that only authorized individuals can reach sensitive data.
Clear Policies and Procedures outlining security expectations and protocols are essential. Employees should understand the consequences of violating security guidelines. Having well-documented processes in place for reporting suspicious activity can help detect potential issues early, preventing larger problems later on.
Continuous Monitoring and Auditing is another critical strategy. By tracking user activity, companies can identify unusual patterns that may signal an issue. Automated systems help monitor behavior in real-time, ensuring that any deviations from normal activity are addressed immediately.
Understanding Risk Detection Evaluation Formats

Evaluating an organization’s ability to identify and respond to internal security risks is essential for maintaining a secure environment. Various methods are used to assess employees’ knowledge and readiness to handle potential issues, from quizzes to scenario-based exercises. Understanding the structure of these evaluations is key to preparing staff and ensuring effectiveness.
Types of Evaluation Formats
Risk detection evaluations come in several forms, each designed to test specific knowledge or reactions. Common formats include:
- Multiple-Choice Questions: These assessments typically cover theoretical concepts and best practices. They help determine an employee’s understanding of potential security risks and responses.
- Scenario-Based Simulations: These exercises immerse employees in simulated situations where they must respond to potential security issues. They assess how well employees apply their knowledge in real-world scenarios.
- Practical Assessments: These involve hands-on tasks, where participants must demonstrate their ability to follow security protocols or identify unusual behavior in a controlled environment.
How These Evaluations Improve Preparedness

By regularly participating in these evaluations, employees are better prepared to spot risks and respond quickly. The more varied and realistic the scenarios, the more effective the training becomes. These assessments not only test knowledge but also build confidence in handling situations as they arise in the workplace.