SSH (Secure Shell) is a popular protocol used for remote login and secure file transfers over unsecured networks. It provides strong encryption and authentication mechanisms to protect sensitive information from being intercepted and compromised. However, as with any technology, there are vulnerabilities that can be exploited by attackers to gain unauthorized access to systems.
Ssh penetration testing is the process of evaluating the security of SSH implementations by simulating the actions of an attacker. This testing helps identify weaknesses or misconfigurations that could potentially be exploited by malicious actors.
Penetration testers use a combination of manual techniques and automated tools to identify vulnerabilities in SSH implementations. They may attempt to exploit known vulnerabilities, test for weak encryption algorithms or authentication mechanisms, and check for misconfigured SSH servers.
By performing ssh penetration testing, organizations can proactively identify and fix security issues before they can be exploited by attackers. This helps improve the overall security posture of SSH implementations and protects sensitive data from unauthorized access.
Ssh Penetration Testing
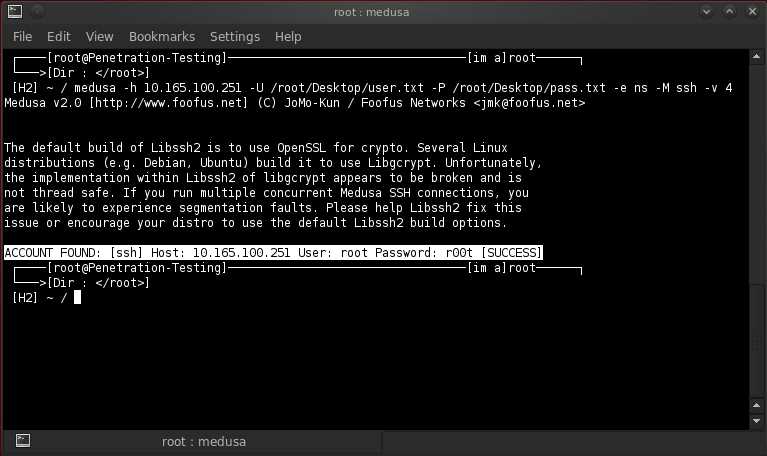
SSH (Secure Shell) is a widely used secure protocol for remote administration of Unix-like systems. It provides strong encryption and authentication mechanisms, making it a popular choice for securing network communications. However, like any other software, SSH implementations may have vulnerabilities that can be exploited by attackers. To ensure the security of SSH implementations, penetration testing is performed to identify and fix any vulnerabilities before they can be exploited by malicious actors.
During SSH penetration testing, several techniques are employed to assess the security of an SSH implementation. One common technique is to perform a vulnerability scan to identify any known vulnerabilities in the SSH server software. This can be done using tools such as Nessus or OpenVAS, which scan the target system for known vulnerabilities and provide a report of any vulnerabilities found.
Another important aspect of SSH penetration testing is to check for weak or default SSH configurations. This includes checking if the SSH server is running on the default port (22) or if weak authentication methods such as password-based authentication are enabled. It is recommended to use strong authentication methods such as public key authentication and disable weak or unnecessary SSH server configurations to enhance security.
Additionally, SSH penetration testing often involves attempting to gain unauthorized access to the target system using techniques such as password guessing, brute-force attacks, or exploiting SSH vulnerabilities. This is done to test the effectiveness of the existing security controls and identify potential weaknesses that could be exploited by attackers.
In summary, SSH penetration testing is a crucial part of securing network communications and ensuring the integrity and confidentiality of remote administration. By identifying and fixing vulnerabilities in SSH implementations, organizations can prevent unauthorized access and protect their systems from potential attacks.
Overview of Ssh Penetration Testing
SSH (Secure Shell) is a widely used protocol for secure remote administration of systems and secure file transfers. It provides strong encryption and authentication, making it an attractive target for attackers. To ensure the security of SSH implementations, extensive penetration testing is conducted to identify vulnerabilities and weaknesses that could be exploited by malicious actors.
Penetration testing is the process of simulating real-world attacks to uncover vulnerabilities in a system. When it comes to SSH, penetration testing involves evaluating the security configurations, authentication mechanisms, and encryption protocols. It also includes testing for common attack vectors such as brute-forcing, dictionary attacks, and client-side vulnerabilities.
Security configurations: Penetration testers assess the SSH server’s configuration to ensure that secure practices are followed. They check for common misconfigurations like weak password policies, incorrect permissions on SSH files, and inappropriate use of protocols and algorithms.
Authentication mechanisms: Testing the authentication mechanisms of SSH involves attempting different methods of authentication to determine their effectiveness. This includes testing password-based authentication, key-based authentication, and multi-factor authentication. Weak authentication mechanisms can provide an entry point for unauthorized access.
Encryption protocols: The encryption protocols used in SSH play a vital role in ensuring the confidentiality and integrity of the data transferred over the network. Penetration testers evaluate the strength of the encryption algorithms used by the SSH server and client, ensuring they are not susceptible to cryptographic attacks.
Attack vectors: Penetration testers attempt various attack techniques to gain unauthorized access to SSH-protected systems. This includes brute-forcing password-based authentication, exploiting vulnerabilities in the SSH client software, and attempting to intercept SSH traffic to capture sensitive information.
Conclusion: SSH penetration testing is crucial for identifying vulnerabilities in SSH implementations and ensuring the security of remote administration and file transfer systems. By conducting thorough penetration tests, organizations can proactively address weaknesses and strengthen their SSH configurations, minimizing the risk of unauthorized access and data breaches.
Preparation for Ssh Penetration Testing
When conducting Secure Shell (SSH) penetration testing, proper preparation is crucial to ensure the success of the testing and to minimize any potential risks or disruptions to the system being tested. This involves several key steps that should be followed before starting the actual penetration testing process.
1. Obtain proper authorization: Before performing any SSH penetration testing, it is essential to obtain proper authorization from the owner of the system or network being tested. This can be done by drafting a formal authorization letter or agreement that clearly outlines the scope, goals, and timeframe of the testing. Without proper authorization, conducting SSH penetration testing can be considered illegal and can result in severe consequences.
2. Identify testing objectives: It is vital to clearly define the objectives of the SSH penetration testing. This includes determining the specific vulnerabilities or weaknesses that need to be tested, the systems or networks that will be targeted, and the impact or potential risks associated with exploiting these vulnerabilities. This step is crucial in directing the testing efforts and ensuring that the desired goals are met.
3. Gather relevant information: The next step is to gather all relevant information about the target system or network. This includes details such as IP addresses, hostnames, port numbers, SSH version, configuration settings, and any other information that may be useful during the testing process. This information can be collected through various methods, including network scans, reconnaissance, and information gathering tools and techniques.
4. Set up a testing environment: To conduct SSH penetration testing safely and effectively, it is essential to set up a controlled testing environment. This environment should mimic the target system or network as closely as possible and should be isolated from any production systems to prevent any unintended disruptions. This can be done by using virtual machines or separate testing networks.
5. Use proper testing tools: There are numerous tools available that can assist in conducting SSH penetration testing. These tools range from basic port scanners to advanced vulnerability scanners and exploit frameworks. It is important to select the appropriate tools based on the testing objectives and the specific vulnerabilities being targeted.
6. Document and report findings: Throughout the testing process, it is crucial to keep detailed documentation of all steps taken, vulnerabilities identified, and any successful exploitation attempts. This documentation will serve as an essential reference and will help in providing a comprehensive report of the findings, along with recommended mitigation strategies or countermeasures.
By following these preparation steps, SSH penetration testing can be conducted in a structured and organized manner, leading to more accurate results and increased security for the tested system or network.
Methods for Ssh Penetration Testing
SSH (Secure Shell) is a widely used protocol for securing remote system administration and file transfers. However, it is not immune to vulnerabilities and can be targeted by attackers. Penetration testing can help identify these vulnerabilities and ensure the security of SSH connections. There are several methods that can be used for SSH penetration testing.
1. Password-based Authentication
One approach to SSH penetration testing is to perform password-based authentication. This involves attempting to log in to the SSH server using a list of common or weak passwords. The goal is to identify any weak passwords that may be used by system administrators or users. This method can be automated using password cracking tools that try different combinations of passwords until a match is found.
2. Brute Force Attacks
A more intensive approach to SSH penetration testing is to perform brute force attacks. This involves systematically trying all possible combinations of usernames and passwords until a successful login is achieved. This method requires a considerable amount of computational power and time, but it can be effective in identifying weak authentication mechanisms.
3. Key-based Authentication
Another method for SSH penetration testing is to target the key-based authentication mechanism. This involves attempting to guess or crack the private key used for authentication. Key-based authentication is often considered more secure than password-based authentication, but it is not immune to attacks. Penetration testers can use tools to try to guess the private key or perform cryptographic attacks to crack it.
4. Vulnerability Scanning
In addition to targeting specific authentication mechanisms, SSH penetration testing can also involve vulnerability scanning. This method involves scanning the SSH server for known vulnerabilities or misconfigurations that could be exploited by attackers. Vulnerability scanning tools can help identify issues such as outdated software versions, weak ciphers, or insecure settings that can be abused to gain unauthorized access.
Overall, SSH penetration testing can help organizations assess the security of their SSH implementations and identify potential weaknesses. It is important to regularly perform these tests to stay ahead of attackers and ensure the integrity and confidentiality of SSH connections.
Common Vulnerabilities in Ssh
SSH (Secure Shell) is a widely used protocol for secure remote login from one computer to another. Despite its reputation for security, there are common vulnerabilities that can be exploited by attackers to gain unauthorized access.
One common vulnerability in SSH is weak passwords. Many users fail to choose strong passwords, making it easier for attackers to guess or crack them. This can lead to unauthorized access to the SSH server and potential compromise of the entire system. It is important for users to choose strong passwords that include a combination of uppercase and lowercase letters, numbers, and special characters.
1. Outdated SSH versions
Using outdated versions of SSH software can also pose a security risk. Older versions may have known vulnerabilities that attackers can exploit to gain unauthorized access. It is essential to regularly update SSH software to the latest version to mitigate these vulnerabilities.
2. Misconfiguration
Misconfigurations can also introduce vulnerabilities in SSH. For example, allowing root login via SSH or allowing SSH with password authentication instead of key-based authentication can increase the likelihood of unauthorized access. It is important to configure SSH properly, following best practices and restricting access to authorized users.
3. Weak encryption algorithms
Using weak encryption algorithms in SSH can also make it easier for attackers to compromise the system. It is important to ensure that strong encryption algorithms, such as AES, are enabled and weaker ones are disabled to minimize the risk of unauthorized access.
4. Open SSH ports
Leaving SSH ports open to the internet without any additional security measures can expose the system to attacks. Attackers can scan for open SSH ports and attempt to brute-force or exploit vulnerabilities to gain access. It is recommended to use firewalls and network segmentation to restrict access to SSH ports and limit the exposure to potential attacks.
By understanding and addressing these common vulnerabilities, users can enhance the security of their SSH connections and protect their systems from unauthorized access.
Tools for Ssh Penetration Testing
Ssh penetration testing involves assessing the security of remote servers by attempting to gain unauthorized access through SSH (Secure Shell) protocols. There are several tools available that can aid in conducting effective SSH penetration tests, providing valuable insights and identifying vulnerabilities. These tools enable security professionals to evaluate the strength of SSH configurations and identify potential risks that may allow unauthorized access.
Nmap is a versatile and widely-used tool that can be utilized for SSH penetration testing. It provides a comprehensive scanning and detection capability, allowing security professionals to identify open ports and potential vulnerabilities on remote servers. By scanning for SSH services, Nmap can help identify potential issues such as weak password configurations or outdated SSH server versions.
Hydra is another powerful tool commonly used in SSH penetration testing. It is a password-cracking tool that can perform brute-force attacks on SSH servers to test the strength of passwords. By automating the process of attempting multiple login combinations, Hydra can help identify weak passwords and password configurations that could be exploited by attackers.
Metasploit Framework can also be utilized for SSH penetration testing. It is an open-source framework that provides a wide range of tools and exploits for testing and identifying security vulnerabilities. With Metasploit, security professionals can launch SSH-related attacks, such as dictionary attacks or exploit modules, to assess the vulnerability of SSH configurations and identify potential weaknesses.
In addition to these tools, secure shell scanners like SSHScan or SSH Auditor can also be helpful in SSH penetration testing. These tools aim to identify misconfigurations, weak ciphers, and other vulnerabilities related to SSH configurations, providing a comprehensive assessment of server security.
In conclusion, utilizing tools like Nmap, Hydra, Metasploit Framework, and secure shell scanners can greatly enhance the effectiveness of SSH penetration testing. These tools enable security professionals to identify vulnerabilities, weaknesses, and misconfigurations in SSH protocols, ensuring the security of remote servers.
Best Practices for Ssh Penetration Testing – Conclusion
SSH penetration testing is a crucial activity for organizations to ensure the security of their networks and systems. By following best practices, organizations can identify vulnerabilities and take appropriate measures to protect their assets.
During SSH penetration testing, it is important to:
- Conduct proper reconnaissance to gather information about the target SSH server.
- Use different scanning techniques to identify potential vulnerabilities.
- Perform thorough enumeration to gather more information about the target system.
- Exploit vulnerabilities, but only with proper authorization.
- Document all findings and make recommendations for improvements.
- Follow ethical guidelines and legal regulations.
Additionally, it is essential to stay up to date with the latest SSH security best practices, as new vulnerabilities and attack techniques constantly emerge.
Ultimately, SSH penetration testing is an ongoing process and should be performed regularly to ensure continuous security of the organization’s systems and networks. By following best practices and staying vigilant, organizations can mitigate risks and protect their valuable assets.